Setup AWS IAM user
It is a good security (and recommended) practice to create a user on AWS other than your root account. And use the new account key pairs in your AWS and Koding accounts and Stacks. To learn more about AWS account best practices read more here.
As Koding for Teams creates & manages your AWS resources, it will use EC2, S3 and EBS services from your AWS account. Of course exact services used depends on your Stack script.
There are two required policies that need to be enabled for the new IAM user to be able to create & build Stacks using EC2s.
- AmazonEC2FullAccess
- IAMReadOnlyAccess
The steps are:
- Create a new user (make sure to generate the Access Keys and save them)
- Create a new group and add the user to this group
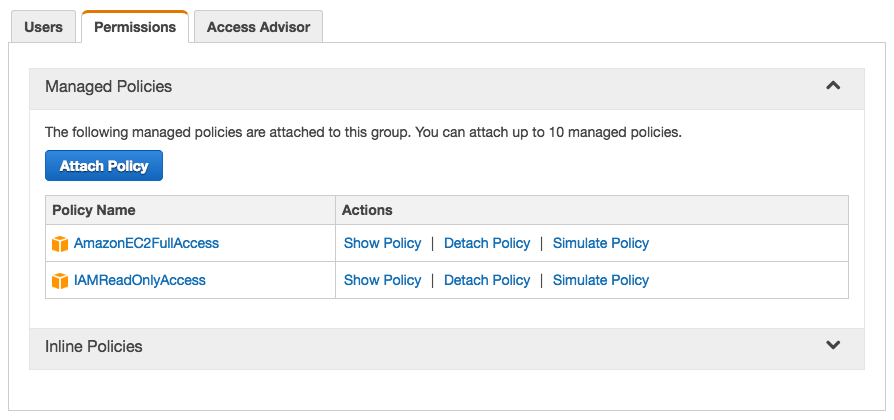
- Assign the above two policies (see screenshot) to the created group
Now you can use the new user Access and Secret Keys with your Koding account in the AWS credentials tab to build your stacks.
Step by step guide
- Log in to your AWS account, choose Services, then choose IAM (Identity and Access Management)
- Create a new user
-
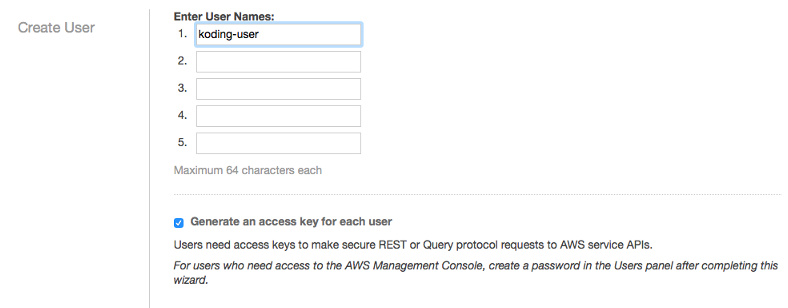
Choose a user name, we created a user called “koding-user”. We also made sure that Generate an access key for each user is enabled
-
Click Show User Security Credentials
-
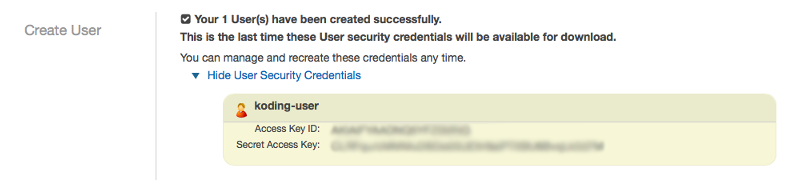
Save the user’s keys (you can also download them) and click close
-
User koding-user created successfully
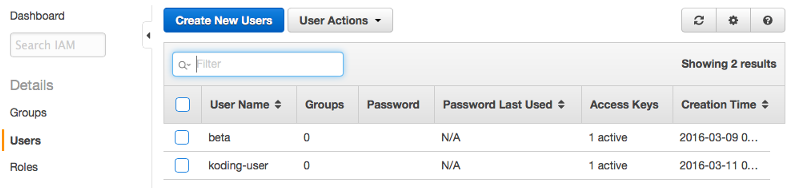
-
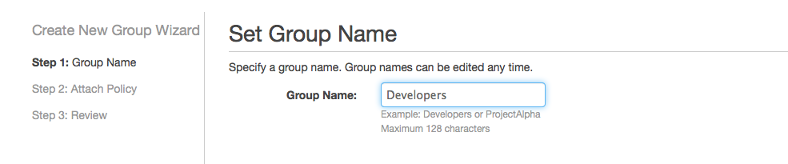
- Create a new group and follow the online wizard
-
Choose a group name, we choose the name “Developers”
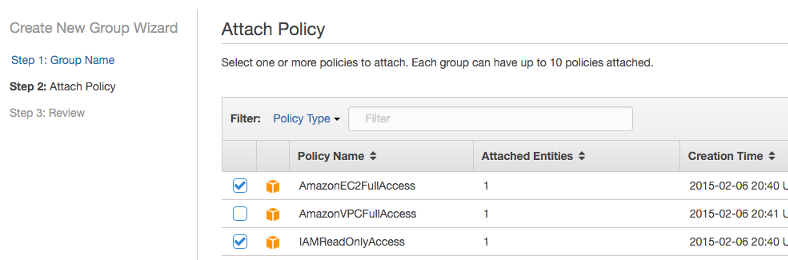
- Choose the access policies
- AmazonEC2FullAccess
- IAMReadOnlyAccess
-
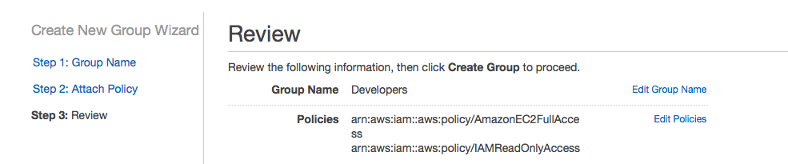
Review and click create
-
- Add the user to the group
-
Go to the Users tab, select and check the user you created and click User Actions -> Add Users to Group
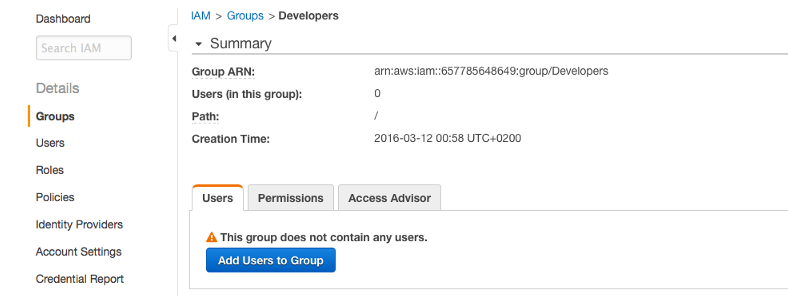
-
Select the koding-user we just created
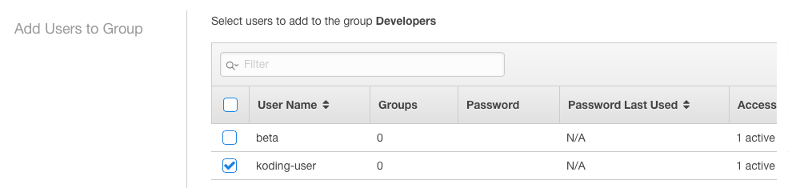
-
User was added to group successfully
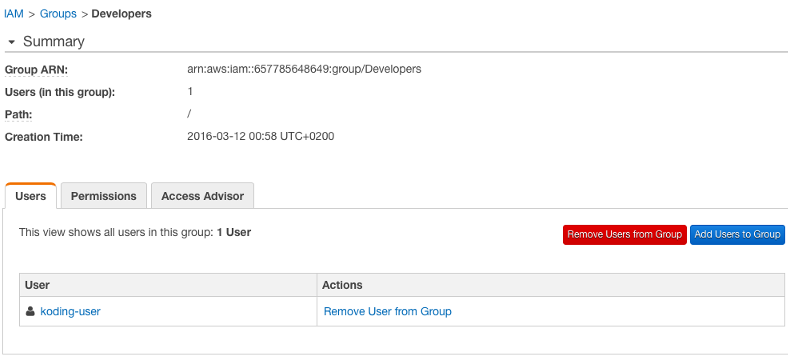
-
Congratulations! You have now created a user on AWS with the required access permissions to build stacks without sacrificing your root user account.
If you want to use Route53 or special settings in AWS, you must extend the Permissions capabilities of the group you just created. Otherwise you and your team will receive an error while building the stack that the user does not have enough permission to carry out those actions. For example, if you are creating an AMI user to use with a Route53 stack setup (check our Route53 guide!) you would need to add the below permissions to the AWS IAM user/group
- AmazonRoute53FullAccess
- AmazonRoute53DomainsFullAccess